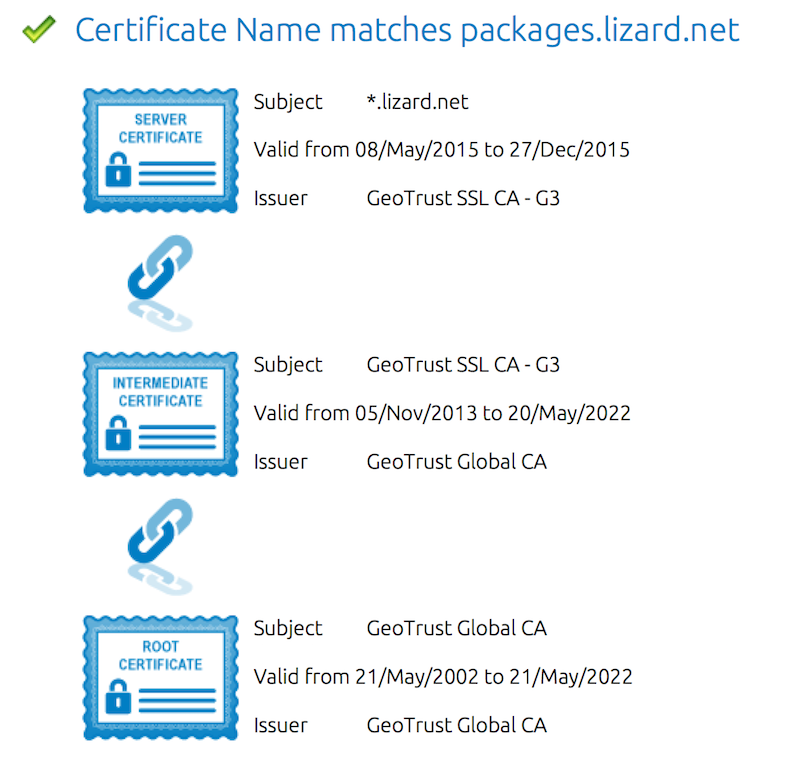
Chain Certificate File . This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. What is the ssl certificate chain? Multiple certificates are in the full ssl chain, and they work in this order: Common file extensions, visual examples, and conversion. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. There are two types of certificate authorities (cas): For an ssl certificate to be trusted, that certificate must have been. Pem files are used to store ssl certificates and their associated private keys. Root cas and intermediate cas. How to recognize and work with pem and der digital certificate files: Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the.
from reinout.vanrees.org
Root cas and intermediate cas. Multiple certificates are in the full ssl chain, and they work in this order: Common file extensions, visual examples, and conversion. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. For an ssl certificate to be trusted, that certificate must have been. How to recognize and work with pem and der digital certificate files: This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. What is the ssl certificate chain? Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation.
Fixing SSL certificate chains Reinout van Rees
Chain Certificate File Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. What is the ssl certificate chain? Root cas and intermediate cas. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Multiple certificates are in the full ssl chain, and they work in this order: Common file extensions, visual examples, and conversion. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. For an ssl certificate to be trusted, that certificate must have been. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. Pem files are used to store ssl certificates and their associated private keys. How to recognize and work with pem and der digital certificate files: This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. There are two types of certificate authorities (cas):
From sectigostore.com
What Is an SSL Certificate Chain & How Does It Work? InfoSec Insights Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. How to recognize and work with pem and der digital certificate files: Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Root cas and intermediate cas. What is the ssl certificate chain? Pem. Chain Certificate File.
From sectigostore.com
What Is an SSL Certificate Chain & How Does It Work? InfoSec Insights Chain Certificate File Root cas and intermediate cas. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. For an ssl certificate to be trusted, that certificate must. Chain Certificate File.
From blog.codyrichardson.io
Certificate Format Basics Chain Certificate File This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Root cas and intermediate cas. Pem files are used to store ssl certificates and their associated private keys. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc. Chain Certificate File.
From shundehai.en.made-in-china.com
44mm Marine Alloy Steel Anchor Chain with Nk Certificate China Anchor Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. Common file extensions, visual examples, and conversion. Multiple certificates are in the full ssl chain, and they work in this order: There are. Chain Certificate File.
From wiki.zimbra.com
Certificate Chain Zimbra Tech Center Chain Certificate File Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. For an ssl certificate to be trusted, that certificate must have been. Multiple certificates. Chain Certificate File.
From sushildpawar.blogspot.com
What is certificate chains and how does certificate chains work. Chain Certificate File Pem files are used to store ssl certificates and their associated private keys. What is the ssl certificate chain? There are two types of certificate authorities (cas): This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. How to recognize and work with pem and der digital certificate files: Common file extensions, visual. Chain Certificate File.
From eocgroup.com
Renewal Supply Chain Certificate EOC Group Chain Certificate File Multiple certificates are in the full ssl chain, and they work in this order: Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. How to recognize and work with pem and der digital certificate files: Common file extensions, visual examples, and conversion. What is. Chain Certificate File.
From es.slideshare.net
Supply Chain Certificate (1) Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. Multiple certificates are in the full ssl chain, and they work in this order: Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. Root cas and intermediate cas. What is the ssl. Chain Certificate File.
From www.stihlusa.com
Saw Chain Identification Guides & Projects STIHL USA Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. Common file extensions, visual examples, and conversion. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. What is the ssl certificate chain? Certificate chain is an ordered list of certificates, containing an ssl/tls. Chain Certificate File.
From cheapsslweb.com
What is a Certificate Authority (CA) in PKI? Chain Certificate File This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Multiple certificates are in the full ssl chain, and they work in this order: What. Chain Certificate File.
From www.thesecuritybuddy.com
What is a Certificate Chain and how does it work? The Security Buddy Chain Certificate File How to recognize and work with pem and der digital certificate files: Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. For an ssl certificate to be trusted, that certificate must have been. Pem files are used to store ssl certificates and their associated. Chain Certificate File.
From reinout.vanrees.org
Fixing SSL certificate chains Reinout van Rees Chain Certificate File Common file extensions, visual examples, and conversion. Root cas and intermediate cas. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. There are two types of certificate authorities (cas): This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate. Chain Certificate File.
From www.oflox.com
Your Guide to The Certificate Chain of Trust The AtoZ Guide! Chain Certificate File Common file extensions, visual examples, and conversion. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Root cas and intermediate cas. For an ssl certificate to be trusted, that certificate must have been. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority. Chain Certificate File.
From www.certificatestemplatesfree.com
Certificate Chain certificates templates free Chain Certificate File Common file extensions, visual examples, and conversion. There are two types of certificate authorities (cas): Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and. Chain Certificate File.
From hartnackandco.com
Personalised Certificate Holder/Folder Custom Made H&Co Chain Certificate File This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. For an ssl certificate to be trusted, that certificate must have been. How to recognize and work with pem and der digital certificate files: There are two types of certificate authorities (cas): Pem files are used to store ssl certificates and their associated. Chain Certificate File.
From theartof12.blogspot.com
the Art of 12 Why HTTPS and SSL are not as secure as you think Chain Certificate File Common file extensions, visual examples, and conversion. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Root cas and intermediate cas. How to recognize and work with pem. Chain Certificate File.
From expeditedsecurity.com
Why you're always at least two steps down your HTTPS certificate chain Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Multiple certificates are in the full ssl chain, and they. Chain Certificate File.
From www.certificatestemplatesfree.com
Certificate File certificates templates free Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Multiple certificates are in the full ssl chain, and they work in this order: How to recognize and work with pem and der digital. Chain Certificate File.
From www.thesslstore.com
How to Combinine Multiple Intermediate Certificates The SSL Store™ Chain Certificate File How to recognize and work with pem and der digital certificate files: This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. For an ssl certificate to be trusted, that certificate must have been. Common file extensions, visual examples, and conversion. This article explains how to include the whole certificate chain (so your. Chain Certificate File.
From www.hotzxgirl.com
Exploring Ssl Certificate Chain With Examples Howtouselinux Hot Sex Chain Certificate File This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. Pem files are used to store ssl certificates and their associated private keys. How to recognize and work. Chain Certificate File.
From venafi.com
What Is a Certificate Chain & How Do They Work? Venafi Chain Certificate File Pem files are used to store ssl certificates and their associated private keys. Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Multiple certificates are in the full ssl chain, and they work in this order: This article contains multiple sets of instructions that walk. Chain Certificate File.
From community.cisco.com
What is the Certificate Chain of Trust? Cisco Community Chain Certificate File What is the ssl certificate chain? Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. Multiple certificates are in the full ssl chain, and they work in this order: Certs should be followed by the issuing cert until the last cert is issued by. Chain Certificate File.
From support.f5.com
SSL Chain Example Chain Certificate File Pem files are used to store ssl certificates and their associated private keys. There are two types of certificate authorities (cas): Common file extensions, visual examples, and conversion. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Multiple certificates are in the full ssl chain, and they work in this order: What. Chain Certificate File.
From cheapsslweb.com
What is SSL Certificate Chain in PKI and How It Works? [Guide] Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. Pem files are used to store ssl certificates and their associated private keys. How to recognize and work with pem and der digital certificate files: What is the ssl certificate chain? This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation.. Chain Certificate File.
From sectigostore.com
What Is an SSL Certificate Chain & How Does It Work? InfoSec Insights Chain Certificate File Root cas and intermediate cas. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Common file extensions, visual examples, and conversion. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. There are two types of certificate authorities (cas): Pem files. Chain Certificate File.
From pki.uwo.ca
Certificate Chain Western Technology Services Western University Chain Certificate File This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Pem files are used to store ssl certificates and their associated private keys. There are two types of certificate authorities (cas): How to recognize and work with pem and der digital certificate files: Certs should be followed by the issuing cert until the. Chain Certificate File.
From www.nic.in
Certificate Chain National Informatics Centre Chain Certificate File Multiple certificates are in the full ssl chain, and they work in this order: How to recognize and work with pem and der digital certificate files: This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Common file extensions, visual examples, and conversion. Pem files are used to store ssl certificates and their. Chain Certificate File.
From www.upgrad.com
IIT Bombay Certificate Program in Supply Chain Management (SCM) upGrad Chain Certificate File Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Multiple certificates are in the full ssl chain, and they work in this order: How. Chain Certificate File.
From sectigostore.com
What Is an SSL Certificate Chain & How Does It Work? InfoSec Insights Chain Certificate File Root cas and intermediate cas. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. For an ssl certificate to be trusted, that certificate must have been. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Pem files are used to. Chain Certificate File.
From wiki.zimbra.com
Certificate Chain Zimbra Tech Center Chain Certificate File This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Multiple certificates are in the full ssl chain, and they work in this order: Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. How to recognize and work. Chain Certificate File.
From www.officesupplies.lk
Certificate File Office Supplies Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. How to recognize and work with. Chain Certificate File.
From sectigostore.com
What Is an SSL Certificate Chain & How Does It Work? InfoSec Insights Chain Certificate File Certificate chain is an ordered list of certificates, containing an ssl/tls certificate and certificate authority (ca) certificates, that enable the receiver to verify that the. For an ssl certificate to be trusted, that certificate must have been. This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. There are. Chain Certificate File.
From www.linkedin.com
CSCMP Supply Chain Foundations Procurement Professional Certificate on Chain Certificate File This article explains how to include the whole certificate chain (so your “user certificate” with all the “intermediary certificates” and optionally,. Multiple certificates are in the full ssl chain, and they work in this order: Certs should be followed by the issuing cert until the last cert is issued by a known root per ietf's rfc 5246 section 7.4.2. Pem. Chain Certificate File.
From supplychainvideos.com
a Supply Chain Manager Supply Chain Videos Chain Certificate File For an ssl certificate to be trusted, that certificate must have been. There are two types of certificate authorities (cas): This article contains multiple sets of instructions that walk through various.pem file creation scenarios for certificate installation. Pem files are used to store ssl certificates and their associated private keys. Common file extensions, visual examples, and conversion. Certs should be. Chain Certificate File.
From support.dnsimple.com
What is the SSL Certificate Chain? DNSimple Help Chain Certificate File How to recognize and work with pem and der digital certificate files: Multiple certificates are in the full ssl chain, and they work in this order: Pem files are used to store ssl certificates and their associated private keys. What is the ssl certificate chain? For an ssl certificate to be trusted, that certificate must have been. Certificate chain is. Chain Certificate File.