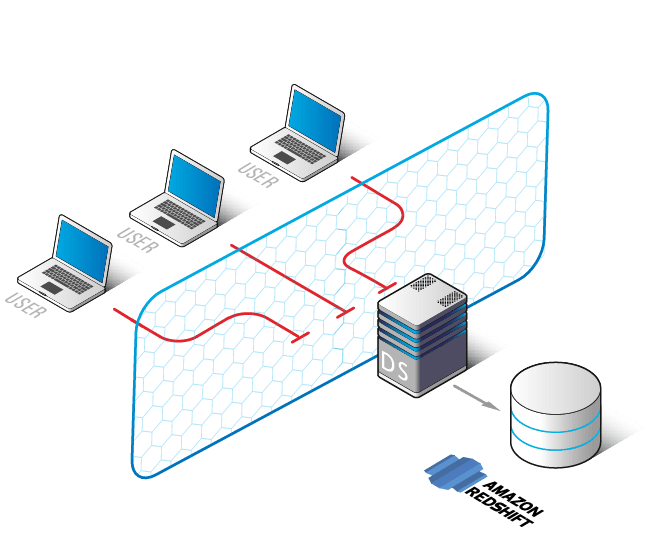
Aws Redshift Security Best Practices . Start creating a new role. Use vpc for secure redshift network environment. Cloud security at aws is the highest priority. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Security best practices for amazon redshift. As an aws customer, you benefit from a data center and network architecture that is built to meet. Another best practice for a secure network for redshift is adding another layer. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Steps 5 to 8 of the ami role creation. This conformance pack contains aws config rules based on amazon.
from www.datasunrise.com
This conformance pack contains aws config rules based on amazon. Another best practice for a secure network for redshift is adding another layer. Use vpc for secure redshift network environment. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Cloud security at aws is the highest priority. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Steps 5 to 8 of the ami role creation. As an aws customer, you benefit from a data center and network architecture that is built to meet.
Amazon Redshift Database Security, DB security for Amazon Redshift
Aws Redshift Security Best Practices Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. As an aws customer, you benefit from a data center and network architecture that is built to meet. Another best practice for a secure network for redshift is adding another layer. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. This conformance pack contains aws config rules based on amazon. Security best practices for amazon redshift. Cloud security at aws is the highest priority. Start creating a new role. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Use vpc for secure redshift network environment. Steps 5 to 8 of the ami role creation.
From pages.awscloud.com
Shift Analytics into High Gear with Tableau and Amazon Redshift Aws Redshift Security Best Practices Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. As an aws customer, you benefit from a data center and network architecture that is built to meet. Start creating a new role. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next”. Aws Redshift Security Best Practices.
From aws.amazon.com
Analyze your Amazon S3 spend using AWS Glue and Amazon Redshift AWS Aws Redshift Security Best Practices This conformance pack contains aws config rules based on amazon. Cloud security at aws is the highest priority. As an aws customer, you benefit from a data center and network architecture that is built to meet. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Use vpc for secure redshift network environment.. Aws Redshift Security Best Practices.
From www.youtube.com
AWS Summit NY 2022 Amazon Redshift security enhancements Protect Aws Redshift Security Best Practices Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Another best practice for a secure network for redshift is adding another layer. This conformance pack contains aws config rules based on amazon. Encryption of data in transit is important to avoid data manipulations, leaks. Aws Redshift Security Best Practices.
From aws.amazon.com
Best Practices for MicroBatch Loading on Amazon Redshift AWS Big Aws Redshift Security Best Practices Another best practice for a secure network for redshift is adding another layer. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb.. Aws Redshift Security Best Practices.
From www.techiexpert.com
Pillars of AWS WellArchitected Framework Aws Redshift Security Best Practices Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Cloud security at aws is the highest priority. Steps 5 to 8 of the ami role creation. Another best practice for a secure network for redshift is adding another layer. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster. Aws Redshift Security Best Practices.
From www.intelligentdiscovery.io
AWS RedShift Enforce SSL Security Best Practice Aws Redshift Security Best Practices Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Steps 5 to 8 of the ami role creation. Use vpc for secure redshift network environment. As an aws customer, you benefit from a data center and network architecture that is built to meet. Cloud. Aws Redshift Security Best Practices.
From zacks.one
AWS Redshift Zacks Blog Aws Redshift Security Best Practices Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. This conformance pack contains aws config rules based on amazon. Security best practices for amazon redshift. Use vpc for secure redshift network environment. As an aws customer, you benefit from a data center and network architecture that is built to meet. Steps 5 to 8 of. Aws Redshift Security Best Practices.
From www.tableau.com
AWS Tableau on Amazon Services for faster analysis Aws Redshift Security Best Practices This conformance pack contains aws config rules based on amazon. Use vpc for secure redshift network environment. Another best practice for a secure network for redshift is adding another layer. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. As an aws customer, you benefit from a data center and network architecture. Aws Redshift Security Best Practices.
From dineshshankar.com
AWS Redshift Best Practices Aws Redshift Security Best Practices Cloud security at aws is the highest priority. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Use vpc for secure redshift network environment. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Another best practice for a secure network for redshift. Aws Redshift Security Best Practices.
From www.allthingsdistributed.com
Amazon Redshift and Designing for Security All Things Distributed Aws Redshift Security Best Practices Security best practices for amazon redshift. This conformance pack contains aws config rules based on amazon. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Steps 5 to 8 of. Aws Redshift Security Best Practices.
From community.microstrategy.com
Amazon Redshift Best Practices for Performance Aws Redshift Security Best Practices Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Cloud security at aws is the highest priority. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Start creating a new role. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws. Aws Redshift Security Best Practices.
From medium.com
AWS IAM Security Best Practices & Checklist by 0xffccdd Medium Aws Redshift Security Best Practices As an aws customer, you benefit from a data center and network architecture that is built to meet. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Start creating a new role. Another best practice for a secure network for redshift is adding another layer. Steps 5 to 8 of the ami role creation. This. Aws Redshift Security Best Practices.
From satoricyber.com
AWS Redshift security access controls explained Satori Aws Redshift Security Best Practices This conformance pack contains aws config rules based on amazon. Another best practice for a secure network for redshift is adding another layer. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Start creating a new role. Redshift allows data movements between the clusters to and clients. Aws Redshift Security Best Practices.
From aws.amazon.com
Build a modern data architecture on AWS with Amazon AppFlow, AWS Lake Aws Redshift Security Best Practices Start creating a new role. This conformance pack contains aws config rules based on amazon. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Cloud security at aws is the highest priority. Encryption of data in transit is important to avoid data manipulations, leaks. Aws Redshift Security Best Practices.
From aws.amazon.com
Modernizing Data Assets from an OnPremises Data Warehouse to Amazon Aws Redshift Security Best Practices Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Cloud security at aws is the highest priority. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such. Aws Redshift Security Best Practices.
From noise.getoto.net
Best practices using AWS SCT and AWS Snowball to migrate from Teradata Aws Redshift Security Best Practices Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Another best practice for a secure network for redshift is adding another layer. Start creating a new role. Use vpc for secure redshift network. Aws Redshift Security Best Practices.
From www.projectpro.io
Learn About the AWS Architecture In Detail with Best Practices Aws Redshift Security Best Practices Use vpc for secure redshift network environment. Steps 5 to 8 of the ami role creation. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Encryption of. Aws Redshift Security Best Practices.
From hevodata.com
AWS Redshift Best Practices for 2021 Learn Hevo Aws Redshift Security Best Practices Cloud security at aws is the highest priority. Steps 5 to 8 of the ami role creation. This conformance pack contains aws config rules based on amazon. Another best practice for a secure network for redshift is adding another layer. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Use vpc for secure redshift network. Aws Redshift Security Best Practices.
From aws.amazon.com
Enhance your security posture by storing Amazon Redshift admin Aws Redshift Security Best Practices This conformance pack contains aws config rules based on amazon. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Steps 5 to 8 of the ami role creation. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Use vpc. Aws Redshift Security Best Practices.
From aws.amazon.com
Store, Protect, Optimize Your Healthcare Data with AWS Part 1 AWS Aws Redshift Security Best Practices Start creating a new role. Security best practices for amazon redshift. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Steps 5 to 8 of the ami role creation. Cloud security at aws is the highest priority. As. Aws Redshift Security Best Practices.
From noise.getoto.net
Get started with data integration from Amazon S3 to Amazon Redshift Aws Redshift Security Best Practices As an aws customer, you benefit from a data center and network architecture that is built to meet. This conformance pack contains aws config rules based on amazon. Another best practice for a secure network for redshift is adding another layer. Start creating a new role. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between. Aws Redshift Security Best Practices.
From dev.classmethod.jp
Amazon Redshift + dbt ユーザー必読の書「Best Practices for Leveraging Amazon Aws Redshift Security Best Practices Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Steps 5 to 8 of the ami role creation. Cloud security at aws is the highest priority. Start creating a new role. Following, you can find best practices for. Aws Redshift Security Best Practices.
From www.simform.com
10 AWS Lambda Use Cases to Start Your Serverless Journey Aws Redshift Security Best Practices Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Start creating a new role. As an aws customer, you benefit from a data center and network architecture that is built. Aws Redshift Security Best Practices.
From geekflare.com
How to Perform AWS Security Scanning and Configuration Monitoring? Aws Redshift Security Best Practices Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Start creating a new role. As an aws customer, you benefit from a data center and network architecture that is built to meet. Security best practices for amazon redshift. Cloud security at aws is the highest priority. Amazon redshift uses ssl for communication. Aws Redshift Security Best Practices.
From hevodata.com
Understanding Amazon Redshift Security 101 Key Features and Practices Aws Redshift Security Best Practices Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Use vpc for secure redshift network environment. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and. Aws Redshift Security Best Practices.
From www.sqlshack.com
Access AWS Redshift from a locally installed IDE Aws Redshift Security Best Practices Cloud security at aws is the highest priority. Start creating a new role. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Another best practice for a secure network for redshift is adding another layer. Use vpc for. Aws Redshift Security Best Practices.
From www.datasunrise.com
Amazon Redshift Database Security, DB security for Amazon Redshift Aws Redshift Security Best Practices Security best practices for amazon redshift. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Start creating a new role. Cloud security at aws is the highest priority. Another best practice for a secure network for redshift is adding another layer. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and. Aws Redshift Security Best Practices.
From support.viurdata.com
Amazon Redshift Viur Support Aws Redshift Security Best Practices Security best practices for amazon redshift. Use vpc for secure redshift network environment. Cloud security at aws is the highest priority. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. This conformance pack contains aws config rules based on amazon. Amazon redshift uses ssl for communication with. Aws Redshift Security Best Practices.
From nightingalehq.ai
What is AWS Redshift? Aws Redshift Security Best Practices Use vpc for secure redshift network environment. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Cloud security at aws is the highest priority. Security best practices for amazon redshift. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. This conformance pack. Aws Redshift Security Best Practices.
From dongtienvietnam.com
Aws Glue Vs Redshift A Comparative Analysis Of Data Warehousing Solutions Aws Redshift Security Best Practices Start creating a new role. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. Use vpc for secure redshift network environment. Another best practice for a secure network for redshift is adding another layer. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Security best practices for amazon redshift. Steps. Aws Redshift Security Best Practices.
From www.youtube.com
AWS REDSHIFT Security Best Practices YouTube Aws Redshift Security Best Practices Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Encryption of data in transit is important to avoid data manipulations, leaks and repudiations. As an aws customer, you benefit from a data center and network architecture that is built to meet. Another best practice for a secure network for redshift is adding another layer. Cloud. Aws Redshift Security Best Practices.
From aws.amazon.com
Automating DBA tasks on Amazon Redshift securely using AWS IAM, AWS Aws Redshift Security Best Practices Another best practice for a secure network for redshift is adding another layer. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. Amazon redshift uses ssl for communication with amazon s3 or amazon dynamodb for copying. Steps 5 to 8 of the ami role. Aws Redshift Security Best Practices.
From dsnews.co.uk
Benefits Of Amazon Redshift Security DS News Aws Redshift Security Best Practices Start creating a new role. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Redshift allows data movements between the clusters to and clients over jdbc/odbc, or between redshift cluster and other aws services such as s3 and dynamodb. This conformance pack contains aws config rules based. Aws Redshift Security Best Practices.
From foghornconsulting.com
What is AWS Redshift Benefits, Use Cases, and Limitations Foghorn Aws Redshift Security Best Practices Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Use vpc for secure redshift network environment. Security best practices for amazon redshift. Cloud security at aws is the highest priority.. Aws Redshift Security Best Practices.
From www.intelligentdiscovery.io
AWS RedShift Enforce SSL Security Best Practice Aws Redshift Security Best Practices Choose “aws service” from the “trusted entity type,” then “redshift” as “use case,” and “next” to continue. Following, you can find best practices for planning a proof of concept, designing tables, loading data into tables, and writing queries for. Start creating a new role. Another best practice for a secure network for redshift is adding another layer. Redshift allows data. Aws Redshift Security Best Practices.