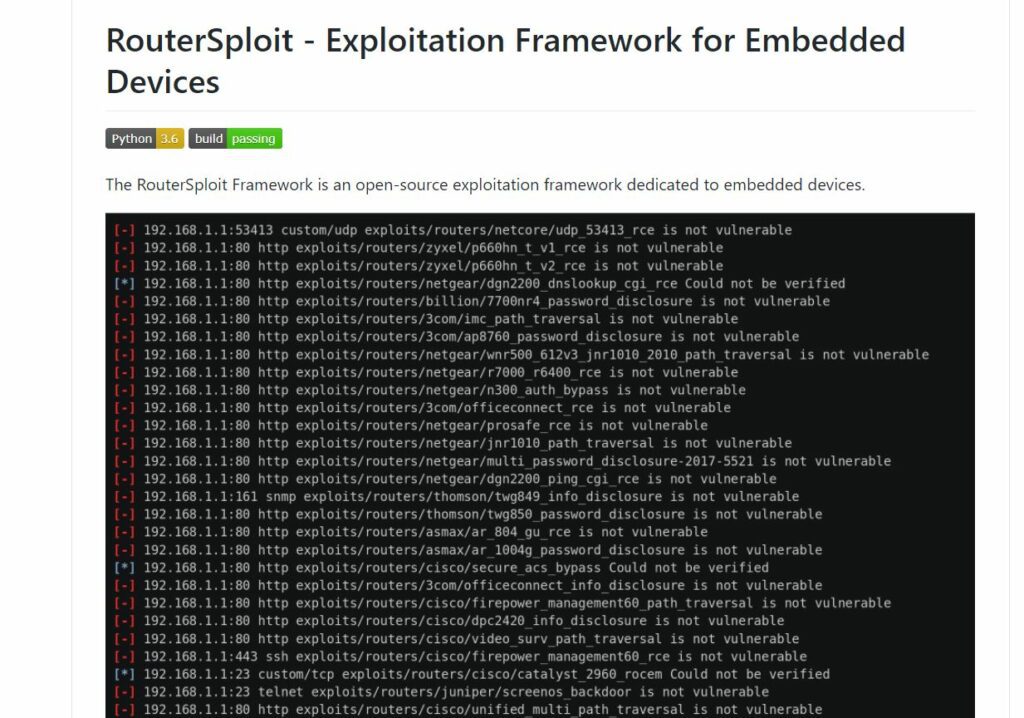
Routersploit Scan . it consists of various modules that aids penetration testing operations: But first, you need to find the router ip of the target router. Both programs are trying to enter the checked device with. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. In this article we will look at its capabilities. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. It consists of various modules that aid.
from iemlabs.com
to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. But first, you need to find the router ip of the target router. It consists of various modules that aid. In this article we will look at its capabilities. it consists of various modules that aids penetration testing operations: The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. Both programs are trying to enter the checked device with. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit.
RouterSploit Cybersecurity Tool IEMLabs Blog Knowledge Base
Routersploit Scan Both programs are trying to enter the checked device with. But first, you need to find the router ip of the target router. It consists of various modules that aid. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. In this article we will look at its capabilities. Both programs are trying to enter the checked device with. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. it consists of various modules that aids penetration testing operations:
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Router, Android phone, Phone Routersploit Scan In this article we will look at its capabilities. It consists of various modules that aid. routersploit and router scan by stas’m programs are designed to compromise routers. But first, you need to find the router ip of the target router. to scan the router against all the possible exploits, we will be using the autopwn scanner module. Routersploit Scan.
From hackeracademy.org
How to exploit routers with Routersploit Hacker Academy Routersploit Scan It consists of various modules that aid. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. Both programs are trying to enter the checked device with. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. . Routersploit Scan.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit Scan it consists of various modules that aids penetration testing operations: to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. It consists of various modules that aid. to scan the router against all the possible exploits, we will be using the autopwn scanner module to. Routersploit Scan.
From www.secuneus.com
Routersploit Secuneus Tech Learn Cyber Security Routersploit Scan Both programs are trying to enter the checked device with. It consists of various modules that aid. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. it consists of various modules that aids penetration testing operations: routersploit and router scan by stas’m programs are. Routersploit Scan.
From gbhackers.com
Exploitation Framework for Embedded devices RouterSploit Routersploit Scan Both programs are trying to enter the checked device with. routersploit and router scan by stas’m programs are designed to compromise routers. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization. Routersploit Scan.
From securitytwins.com
RouterSploit Framework para la auditoría de routers Security Twins Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. It consists of various modules that aid. But first, you need to find the router ip of the target router. In this article we will look at its capabilities. to scan for. Routersploit Scan.
From github.com
GitHub Exploitinstall/routersploit The Router Exploitation Framework Routersploit Scan it consists of various modules that aids penetration testing operations: for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. The tool consists of five modules responsible, in turn, for exploiting. Routersploit Scan.
From hackeracademy.org
How to exploit routers with Routersploit Hacker Academy Routersploit Scan In this article we will look at its capabilities. Both programs are trying to enter the checked device with. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. But first, you. Routersploit Scan.
From fullcrypters.net
RouterSploit Framework de exploração de roteadores FULL CRYPTERS Routersploit Scan The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. it consists of various modules that aids penetration testing operations: In this article we will look at its capabilities. Both programs. Routersploit Scan.
From www.youtube.com
How To Install RouterSploit In Ubuntu/Termux Check The Security Of Your Wifi Router Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans,. Routersploit Scan.
From blog.csdn.net
routersploit简单实例CSDN博客 Routersploit Scan It consists of various modules that aid. But first, you need to find the router ip of the target router. it consists of various modules that aids penetration testing operations: routersploit and router scan by stas’m programs are designed to compromise routers. to scan the router against all the possible exploits, we will be using the autopwn. Routersploit Scan.
From www.youtube.com
RouterSploit Scan Your Wifi Router is Vulnerable or Not ? in hindi YouTube Routersploit Scan It consists of various modules that aid. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. routersploit and router scan by stas’m programs are designed to compromise routers. But first, you need to find the router ip of the target router. In this article we. Routersploit Scan.
From www.youtube.com
Vulnerability Testing Scanning IoT devices for vulnerabilities using Routersploit Framework Routersploit Scan The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. Both programs are trying to enter the checked device with. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our. Routersploit Scan.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Scan It consists of various modules that aid. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. In this article we will look at its capabilities. it consists of various modules that aids penetration testing operations: to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py. Routersploit Scan.
From www.youtube.com
Routersploit Tool Installation in Termux Termux thenoobhacker YouTube Routersploit Scan for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. Both programs are trying to enter the checked device with. it consists of various. Routersploit Scan.
From github.com
GitHub threat9/routersploit Exploitation Framework for Embedded Devices Routersploit Scan Both programs are trying to enter the checked device with. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. But first, you need to find the router ip of the target. Routersploit Scan.
From cyberpointsolution.com
Router and Switches Testing Tools Routersploit Framework Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. routersploit and router scan by stas’m programs are designed to compromise routers. Both programs are trying to. Routersploit Scan.
From null-byte.wonderhowto.com
How to Seize Control of a Router with RouterSploit « Null Byte WonderHowTo Routersploit Scan routersploit and router scan by stas’m programs are designed to compromise routers. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. it consists of various modules that. Routersploit Scan.
From www.youtube.com
RouterSploit Complete Tutorial YouTube Routersploit Scan it consists of various modules that aids penetration testing operations: But first, you need to find the router ip of the target router. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. routersploit and router scan by stas’m programs are. Routersploit Scan.
From www.freebuf.com
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户 Routersploit Scan It consists of various modules that aid. But first, you need to find the router ip of the target router. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. Both programs are trying to enter the checked device with. In this article. Routersploit Scan.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone, Android tutorials, Android Routersploit Scan Both programs are trying to enter the checked device with. In this article we will look at its capabilities. But first, you need to find the router ip of the target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. routersploit and router scan by stas’m programs are designed to compromise routers.. Routersploit Scan.
From www.cyberpunk.rs
Router Exploitation Framework RouterSploit CYBERPUNK Routersploit Scan to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. Both programs are trying to enter the checked device with. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. it consists of various modules that aids penetration testing operations: . Routersploit Scan.
From www.anquanke.com
【技术分享】如何在未root的手机上安装漏洞利用框架RouterSploit安全客 安全资讯平台 Routersploit Scan But first, you need to find the router ip of the target router. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. routersploit and router scan. Routersploit Scan.
From pentestcore.com
آموزش ابزار RouterSploit در تست نفوذ پن تست کور Routersploit Scan But first, you need to find the router ip of the target router. In this article we will look at its capabilities. to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. it consists of various modules that aids penetration testing operations:. Routersploit Scan.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. In this article we will look at its capabilities. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. . Routersploit Scan.
From www.youtube.com
TUTORIAL HOW TO USE ROUTERSPLOIT YouTube Routersploit Scan Both programs are trying to enter the checked device with. In this article we will look at its capabilities. But first, you need to find the router ip of the target router. routersploit and router scan by stas’m programs are designed to compromise routers. to scan the router against all the possible exploits, we will be using the. Routersploit Scan.
From null-byte.wonderhowto.com
How to Seize Control of a Router with RouterSploit « Null Byte WonderHowTo Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. But first, you need to find the router ip of the target router. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules. Routersploit Scan.
From andeandelumoet.blogspot.com
Exploit Router Dengan RouterSploit Di Ubuntu ande ande lumoet Routersploit Scan But first, you need to find the router ip of the target router. it consists of various modules that aids penetration testing operations: routersploit and router scan by stas’m programs are designed to compromise routers. In this article we will look at its capabilities. Both programs are trying to enter the checked device with. to scan for. Routersploit Scan.
From hackware.ru
Инструкция по использованию RouterSploit HackWare.ru Routersploit Scan In this article we will look at its capabilities. It consists of various modules that aid. Both programs are trying to enter the checked device with. But first, you need to find the router ip of the target router. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the. Routersploit Scan.
From iemlabs.com
RouterSploit Cybersecurity Tool IEMLabs Blog Knowledge Base Routersploit Scan Both programs are trying to enter the checked device with. It consists of various modules that aid. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and. Routersploit Scan.
From jarnobaselier.nl
RouterSploit Router Exploitation Framework Jarno Baselier Routersploit Scan it consists of various modules that aids penetration testing operations: But first, you need to find the router ip of the target router. Both programs are trying to enter the checked device with. to scan for vulnerable routers on a specific network range using routersploit, you can use the routersploit.py script with the scan module. to scan. Routersploit Scan.
From www.freebuf.com
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户 Routersploit Scan The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization data, vulnerability scans, generating payloads and modules responsible for generic. routersploit and router scan by stas’m programs are designed to compromise routers. In this article we will look at its capabilities. to scan for vulnerable routers on a specific network range using routersploit,. Routersploit Scan.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone, Router, Computer maintenance Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. In this article we will look at its capabilities. for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. it consists of various modules that aids penetration. Routersploit Scan.
From kali.tools
RouterSploit Инструменты Kali Linux Routersploit Scan to scan the router against all the possible exploits, we will be using the autopwn scanner module to find any vulnerabilities that affect our target router. But first, you need to find the router ip of the target router. Both programs are trying to enter the checked device with. In this article we will look at its capabilities. . Routersploit Scan.
From techglobal7894.blogspot.com
how to hack wifi using routersploit in termux (without root) 2021. Best easy idea Routersploit Scan routersploit and router scan by stas’m programs are designed to compromise routers. But first, you need to find the router ip of the target router. Both programs are trying to enter the checked device with. In this article we will look at its capabilities. The tool consists of five modules responsible, in turn, for exploiting the device, testing authorization. Routersploit Scan.