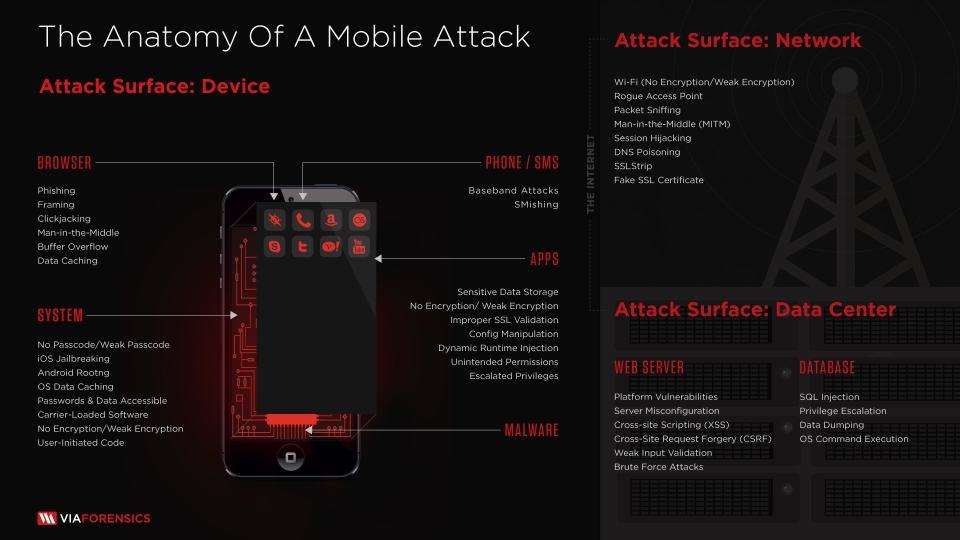
Mobile Device Attack . Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile.
from www.nowsecure.com
Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. These threats often take the form of malware or. The matrices cover techniques involving device.
Anatomy of a Mobile Attack NowSecure
Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. These threats often take the form of malware or. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile.
From www.le-vpn.com
Desafíos De Seguridad En Los Dispositivos Móviles Le VPN Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. In this new paradigm, the mobile device is used. Mobile Device Attack.
From www.zimperium.com
Top 4 Threats to O365 on Mobile Devices (and How to Stop Them) Zimperium Mobile Device Attack The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. These threats often take the form of malware or. In this new paradigm, the mobile device is used more. Mobile Device Attack.
From informationsecurity.wustl.edu
INFOGRAPHIC 20 Ways to Stop Mobile Attacks Office of Information Mobile Device Attack Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks.. Mobile Device Attack.
From www.apogeesolutions.co.uk
Mobile Device Attacks You Need to Be Aware Of Apogee Solutions Mobile Device Attack In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Below are the tactics and techniques representing the two mitre att&ck ® matrices for. Mobile Device Attack.
From threatpost.com
Mobile Risks Boom in a PostPerimeter World Threatpost Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. These threats often take the form of malware or. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. Below are the tactics. Mobile Device Attack.
From www.linkedin.com
Top 5 Mobile Device Attacks You Need to Watch Out For Mobile Device Attack The matrices cover techniques involving device. These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks that are intended to. Mobile Device Attack.
From auth0.com
The 9 Most Common Security Threats to Mobile Devices in 2021 Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. The matrices cover techniques involving device. These threats often take the form of malware or. Below are the tactics. Mobile Device Attack.
From itmtech.ie
Top 5 Mobile Device Attacks You Need to Watch Out For ITM Mobile Device Attack In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Communicating mobile security threats and best practices has become a central objective due to the. Mobile Device Attack.
From www.aryon.com.au
Mobile Device Security Malware Attacks Are Increasing Take These Mobile Device Attack These threats often take the form of malware or. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. The matrices cover techniques involving device. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Communicating mobile security threats and best practices has become a. Mobile Device Attack.
From bitsconsulting.net
Top 5 Mobile Device Attacks You Need to Watch Out For BITS Consulting LLC Mobile Device Attack These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more. Mobile Device Attack.
From swimlane.com
Discover the 5 Major Mobile Device Security Threats Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. These threats often take the form of malware. Mobile Device Attack.
From www.mactech.com
Every enterprise has mobile security attacks, threats Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more than ever to. Mobile Device Attack.
From educatererindia.blogspot.com
Mobile Security Mobile Device Attack These threats often take the form of malware or. The matrices cover techniques involving device. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm,. Mobile Device Attack.
From klik.solutions
Mobile device attacks to watch out for Klik.Solutions Mobile Device Attack In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Below are the tactics and techniques representing the two mitre att&ck ® matrices for. Mobile Device Attack.
From it.microchannel.com.au
Mobile Device Attacks You Need to Watch Out For MicroChannel Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. The matrices cover techniques involving device. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new. Mobile Device Attack.
From cybersecuritynews.com
Mobile Devices Attack Increase by 187 Report Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. These threats often take the form of malware or. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Mobile security threats are attacks. Mobile Device Attack.
From copperbandtech.com
How to Defend Against These Common Attacks Hitting Mobile Devices Mobile Device Attack These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Communicating mobile security threats and best practices has become a central objective due to the ongoing. Mobile Device Attack.
From soundcomputers.net
4 Top Mobile Device Attacks Sound Computers Westbrook, CT Mobile Device Attack Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from. Mobile Device Attack.
From www.mymemory.co.uk
5 Steps to Prevent Mobile Malware Attacks MyMemory Blog Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. These threats often take the form of malware or. The matrices cover techniques involving device.. Mobile Device Attack.
From www.dreamstime.com
Infographic for 5 Common Types of Cell Phone Cyber Attacks Stock Vector Mobile Device Attack The matrices cover techniques involving device. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones. Mobile Device Attack.
From www.pinterest.jp
Learn more about Mobile Device Attacks threatinsight Threat, Mobile Mobile Device Attack These threats often take the form of malware or. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Communicating mobile security threats and best practices has become a. Mobile Device Attack.
From auth0.com
The 9 Most Common Security Threats to Mobile Devices in 2021 Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. The matrices cover techniques involving device. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. In this new paradigm, the mobile device is used more than ever to. Mobile Device Attack.
From www.infosectrain.com
Common Wireless and Mobile Device Attacks InfosecTrain Mobile Device Attack In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. These threats often take the form of malware or. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Mobile security threats are attacks. Mobile Device Attack.
From www.tworivercomputer.com
What Are the Most Popular Attacks on Mobile Devices? Mobile Device Attack In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. Below are the tactics and techniques representing the. Mobile Device Attack.
From www.stealthlabs.com
Top 8 Mobile Device Cyber Threats You Should Know to Protect Your Data! Mobile Device Attack These threats often take the form of malware or. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets.. Mobile Device Attack.
From www.kaspersky.com
Android Threats Infographic Mobile Threats Infographics Mobile Device Attack These threats often take the form of malware or. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Below are the tactics and. Mobile Device Attack.
From geek911.com
4 Most Frequent Mobile Device Attacks & How to Protect Against Them Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. These threats often take. Mobile Device Attack.
From interwiseit.com.au
Be Aware of Mobile Device Attacks Interwise IT Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. The matrices cover techniques involving device. Mobile security threats are attacks that are intended to. Mobile Device Attack.
From sabtrax.ca
Attacks on Mobile Devices Are Rising Rapidly Learn What You Need to Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. These threats often take the form of malware or.. Mobile Device Attack.
From www.nowsecure.com
Anatomy of a Mobile Attack NowSecure Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. The matrices cover techniques involving device. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. Below are the tactics and techniques representing the two mitre att&ck ® matrices. Mobile Device Attack.
From realtimeits.co.uk
Top 5 Mobile Device Attacks You Need to Watch Out For Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. Mobile security threats are attacks that are intended. Mobile Device Attack.
From www.pnjsharptech.com
Cyber Attacks on Mobile Devices Methods to Protect Cyber Attacks Mobile Device Attack These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. Mobile security threats are attacks. Mobile Device Attack.
From epx.co.uk
Top 5 Mobile Device Attacks You Need to Watch Out For EPX Mobile Device Attack Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. In this new paradigm, the mobile device is used more than ever to access corporate systems, both for routine as well as for critical tasks. The matrices cover techniques involving device. These threats often take the form of malware. Mobile Device Attack.
From www.youtube.com
What exactly is a mobile DEVICE attack? YouTube Mobile Device Attack These threats often take the form of malware or. Communicating mobile security threats and best practices has become a central objective due to the ongoing discovery of new vulnerabilities of. The matrices cover techniques involving device. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. Mobile security threats are attacks that are intended to. Mobile Device Attack.
From blog.x-centric.com
Top 5 Mobile Device Attacks You Need To Watch Out For Mobile Device Attack Mobile security threats are attacks that are intended to compromise or steal data from mobile devices like smartphones and tablets. These threats often take the form of malware or. Below are the tactics and techniques representing the two mitre att&ck ® matrices for mobile. The matrices cover techniques involving device. In this new paradigm, the mobile device is used more. Mobile Device Attack.