LAN interface
LAN Interface
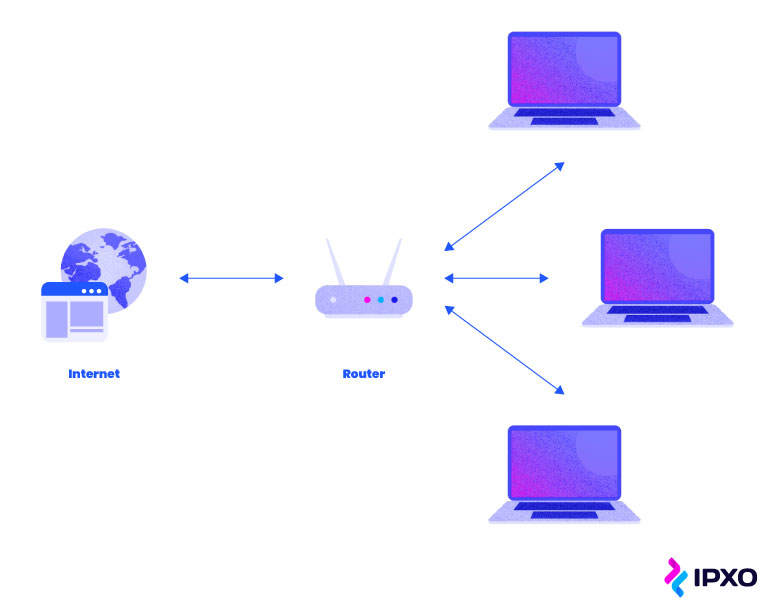
In the current interconnected world, networking has become an essential part of our daily lives. Local Area Network (LAN) is a type of network that provides connectivity within a limited geographic area such as a home, office or small business. A LAN interface is the physical port on the computer system where an Ethernet cable or other network cable can be connected. The LAN interface is required for a computer to communicate with devices on the same network.
The LAN interface provides a means by which data is exchanged between multiple devices connected to the network. The data transfer can be as fast as a few hundred megabits per second or even gigabits per second, depending on the hardware and network setup. The LAN interface connects to the gateway or router, which directs network traffic, and regulates incoming and outgoing data. The router provides connectivity to the internet and other devices outside the LAN.
The LAN interface is usually located on the back of the computer and can be identified by an RJ-45 port or Ethernet port. The Ethernet cable is plugged into this port and connected to another device within the network. Devices that can be connected to the LAN interface include computers, printers, wireless access points or even network-attached storage (NAS) devices.
In conclusion, the LAN interface is a vital component for network communication within a limited geographic area. With constant advancements in networking technology, the LAN interface is becoming faster and more efficient in handling data transfers. For any computer user who needs to share or access data within a network, a functioning LAN interface is a fundamental requirement.