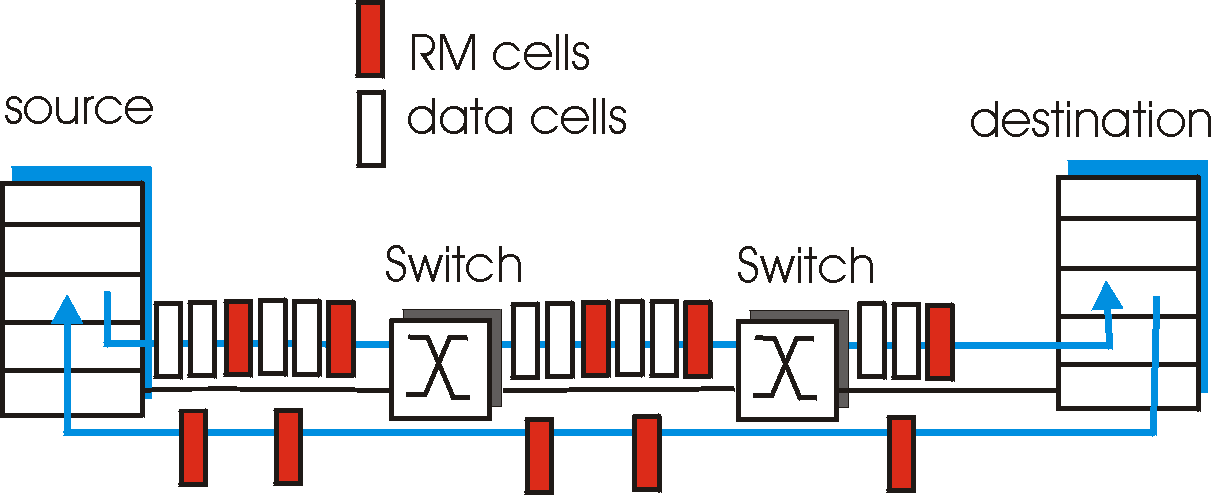
Wireless transmission protocol is a critical element of modern communication technology, enabling the transmission of information without the use of cables or wires. It is a method of transmitting data from one device to another using radio waves, infrared signals, or other wireless communication methods.
The primary advantage of wireless transmission protocol is the ability to transmit information over vast distances without physical connection, unlike traditional wired communication systems. Wireless communication systems allow easy integration of devices without the need for complex wiring. This technology has revolutionized the Internet of Things (IoT), which is a network of interconnected devices that can communicate with one another, facilitating automation and data analysis tasks.
Wireless transmission protocols are essential for the smooth functioning of various wireless communication systems. These protocols include Wi-Fi, Bluetooth, ZigBee, Near Field Communication (NFC), Radio Frequency Identification (RFID), and many more. These protocols have different data transmission rates, operating frequencies, security features, and ranges, which cater to the specific requirements of different applications.
The importance of wireless transmission protocols is evident in various applications, such as home automation, industrial automation, medical networks, agriculture, transportation, and many more. The growing demand for wireless connectivity and the increasing adoption of IoT technology is driving the development and standardization of new wireless protocols and improving existing ones.
Therefore, Wireless transmission protocol is a critical aspect of modern communication technology, enabling seamless communication across devices and networks without physical connections.