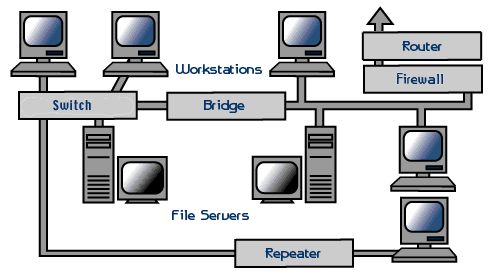
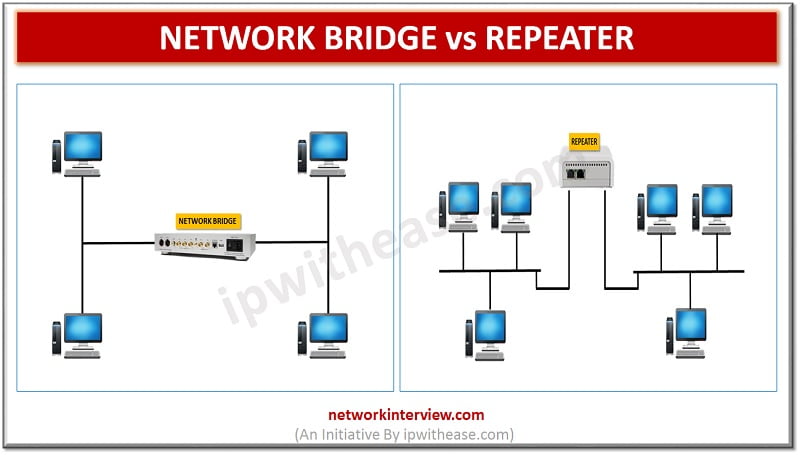
Network security architecture is a vital part of any organization's security strategy. It encompasses the arrangement of devices, software, protocols, and technologies that are used to secure a network infrastructure from unauthorized access, theft, and mismanagement. With the rise of cyber threats and attacks, network security architecture has become more critical than ever.
The first step towards building a strong network security architecture is to understand how data flows through your network. This allows you to identify potential security risks and design security controls to mitigate them. Designating secure zones or securing data paths within the network using firewalls and VPNs is also crucial.
Another key component of network security architecture is access control. This involves verifying that users and devices are who they claim to be. Two-factor authentication, biometrics, and VPNs are all useful tools to achieve this. The goal is to ensure the right people have the right access to the right resources.
Monitoring and response are also vital. The ability to detect and respond to security incidents in real-time can prevent major breaches. Network security architecture should include logging and analysis systems that detect abnormal behavior and potential threats.
Finally, network security architecture is an ongoing process that requires continuous monitoring and refinement. Regular vulnerability assessments, security audits, and penetration testing can help to identify weaknesses and ensure a proactive approach to security.
Overall, network security architecture is critical for any organization's security posture. By adopting a holistic approach that incorporates access control, monitoring, and response, businesses can build a secure network environment that protects against cyber threats and data theft.