Wireless Encryption Method
Wireless encryption is a technology used to secure wireless networks. When data or information is sent over a wireless network, it can be intercepted by hackers or malicious actors. To prevent such intrusions, wireless encryption is employed to secure data by encrypting it. Encryption is a process of converting plain text into cipher text, which is unreadable to unauthorized users.
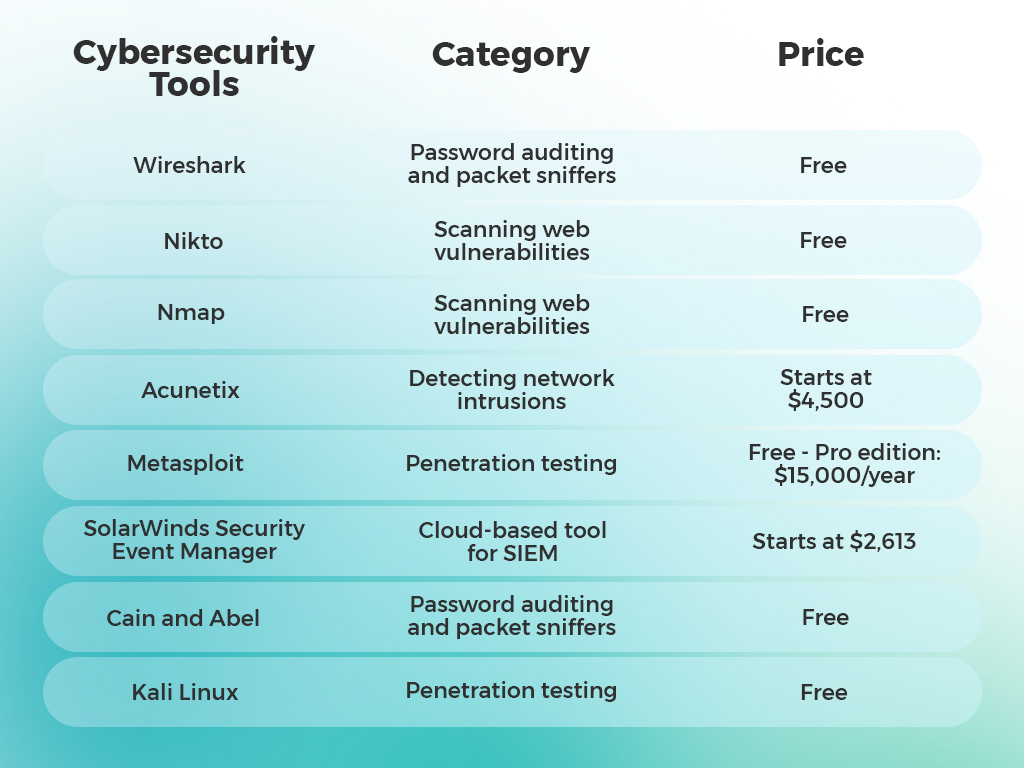
There are several wireless encryption methods, the most popular of which are: WEP, WPA, and WPA2.
WEP (Wired Equivalent Privacy) is the oldest method of wireless encryption. It uses a 40-bit or 128-bit encryption key in hexadecimal format. However, WEP is not considered secure today, as it can be easily hacked by modern tools.
WPA (Wi-Fi Protected Access) was introduced as an improvement to WEP. It uses the Temporal Key Integrity Protocol (TKIP) to address some of the issues with WEP. However, WPA has some security flaws and is not considered as secure as WPA2.
WPA2 (Wi-Fi Protected Access 2) is the most secure method of wireless encryption currently available. It uses a 128-bit encryption key in AES (Advanced Encryption Standard) format. It also uses CCMP (Counter-Mode/CBC-MAC Protocol) to secure data.
To configure wireless encryption, users must login to their router's administration page and select the encryption method. They must then enter the encryption key, which will be used to encrypt the data.
In conclusion, wireless encryption is essential to secure wireless networks. Users should carefully select the encryption method and use the most secure option available, which is WPA2. By doing so, they can ensure that their data is safe from prying eyes.
Router default login
Router Default Login
If you have ever set up a router, you know that you need to log in to it to configure it. Most routers come with a default username and password that you can use to access the settings. However, these default logins are a security risk, as they are well-known and can be easily exploited by hackers. In this article, we will explore the dangers of default logins and how to change them.
Default logins are easy to remember but also easy to guess for anyone who knows the manufacturer and model of your router. Hackers can use this information to gain access to your network and steal sensitive information. They can also use your router to launch attacks on other networks. Therefore, it is essential to change the default username and password as soon as possible.
To change your router's login credentials, you need to log in to the router's web interface using the default username and password. From there, you can navigate to the security settings and choose a new username and password. It is best to use a complex password that includes a mix of numbers, letters, and symbols. You should also avoid using any personal information, such as your name or date of birth, in your password.
In addition to changing the login credentials, it is also a good idea to update the firmware of your router regularly. Firmware updates often include security fixes that can protect your router from known vulnerabilities. You can check for firmware updates in the router's web interface or on the manufacturer's website.
In conclusion, default logins are a significant security risk, and you should change them as soon as possible. Use a complex password and update your router's firmware regularly to stay protected from cyber threats. With these simple steps, you can ensure that your router is secure and your network data stays safe.