Wireless Transmission Security Audit: Ensuring the Safety of Your Network Connection
Wireless transmission is an essential technology that enables individuals and businesses to connect and communicate seamlessly. However, with the broad use of wireless networks, there is a high potential for security risks, including hackers, malware, and data breaches. Therefore, it is essential to conduct a wireless transmission security audit to ensure the safety and security of your network connection.
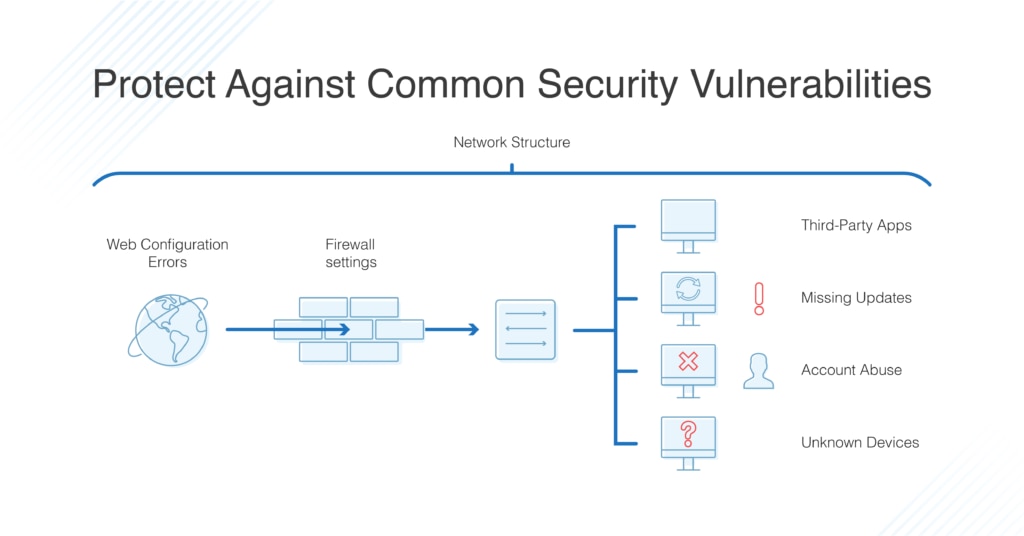
A wireless transmission security audit is a comprehensive review of your network's security controls and infrastructure. The process aims to identify vulnerabilities in your wireless network, assess the effectiveness of your security protocols, and suggest measures to mitigate the risks. The audit covers aspects such as encryption, access control, authentication, and intrusion detection.
One of the benefits of conducting a wireless transmission security audit is that it improves your network's security posture. It provides a detailed assessment of potential threats and vulnerabilities, allowing you to address them before they are exploited. Additionally, a security audit helps you comply with industry standards and regulations such as HIPAA, PCI DSS, and GDPR.
Wireless transmission security audit involves the use of various tools and techniques. For example, a penetration test is a simulation of an attack on your network to identify vulnerabilities. Network scanning helps to detect open ports and services, and wireless intrusion detection system (WIDS) monitors wireless traffic for malicious activity.
In conclusion, conducting a wireless transmission security audit is crucial to ensure the safe and secure operation of your network connection. The audit helps identify security vulnerabilities, improve security control measures, and comply with industry standards and regulations. By investing in a security audit, you can protect your wireless network from potential security risks and safeguard your data and information.