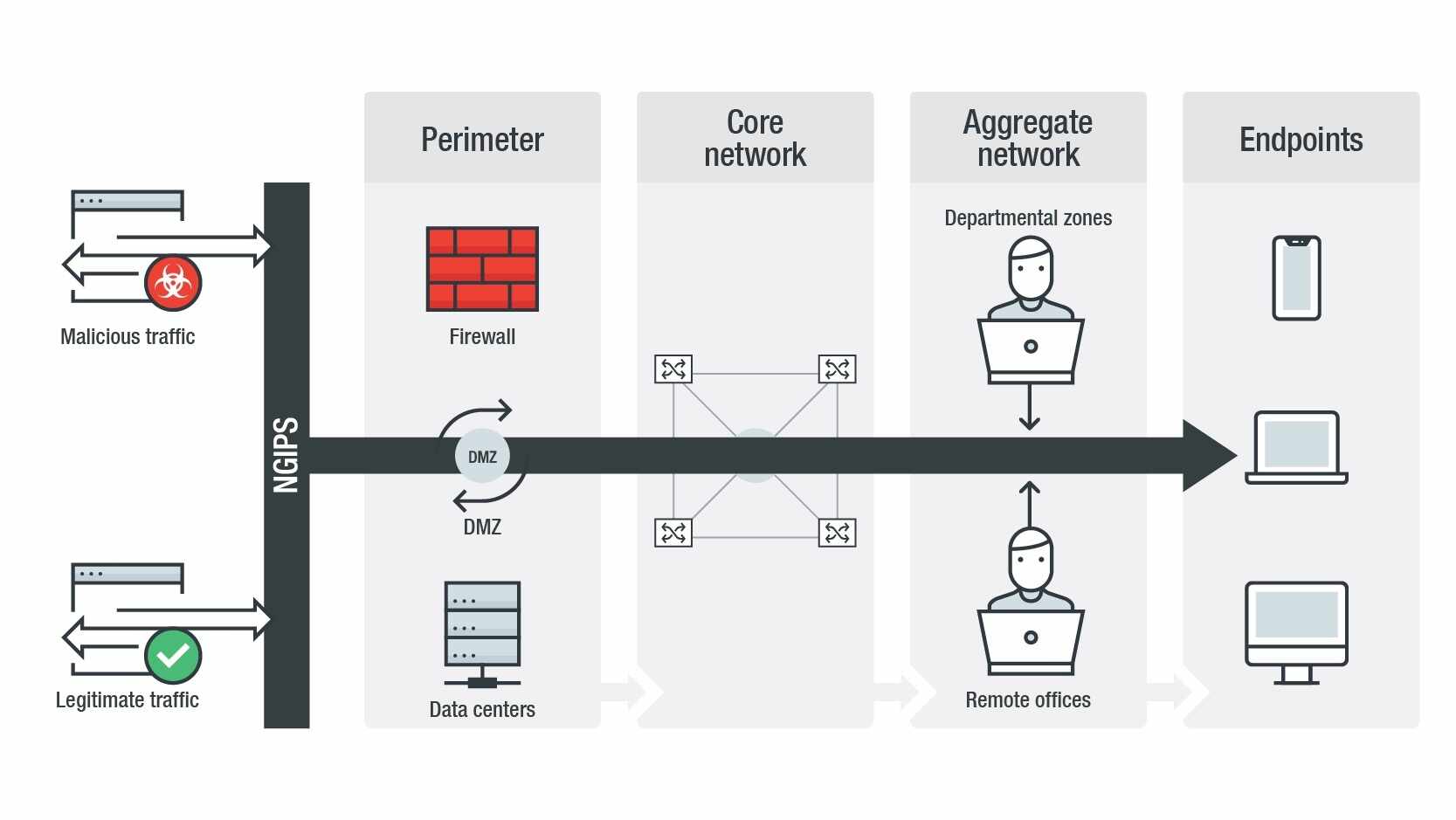
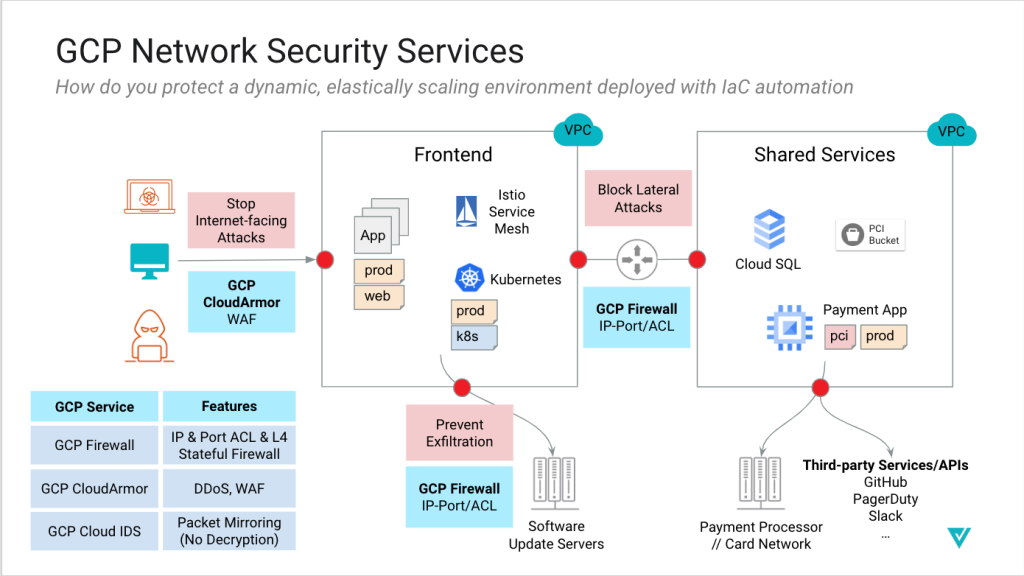
Router Connection Problem
If you are facing issues with your internet connection, there is a high chance that the problem is with your router. A router is an essential piece of hardware that connects all your devices to the internet. When a connection issue arises, it can be frustrating, time-consuming, and even lead to a loss of productivity.
Firstly, you should start by checking the wiring of your router. Ensure that all cables are plugged in correctly and securely. Loose cables can cause a significant disruption in your internet connection. Next, check if your router is receiving power, and if the indicator lights are on. If the lights are off, it means that the router is not receiving power or has malfunctioned.
Another reason why your router may be experiencing connection issues is due to interference from other devices such as microwaves, cordless phones, or even your neighbour's Wi-Fi network. Try to move your router to a different location, away from potential sources of interference.
Updating your router's firmware may also resolve any connectivity issues you are facing. A firmware update ensures that your device is using the latest software, thereby fixing any known bugs or glitches. Check your router manufacturer's website to see if a firmware update is available.
Lastly, if none of the above steps work, try resetting your router. A router reset restores the device to its factory settings, which can help resolve any problem that you are encountering.
In conclusion, there are several methods to troubleshoot router connection problems. If you are still unable to establish a stable internet connection, contact your internet service provider for further assistance.