Keep Your Network Running Smoothly with a Network Monitoring Tool
Is your network experiencing downtime or performance issues? Are you unsure whether your servers and devices are functioning as they should be? If so, it may be time to invest in a network monitoring tool – the solution that can drastically improve your network's health and stability.
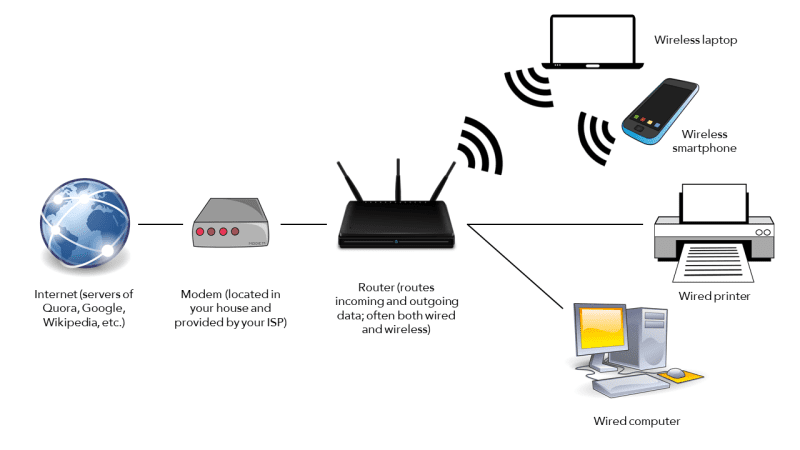
Network monitoring tools are software applications that allow you to monitor your network's performance, identify potential issues, and ensure that all devices are functioning optimally. These tools are designed to provide administrators with real-time data and updates – including traffic statistics, bandwidth utilization, and error logs – so that they can respond quickly to any issues that arise.
There are many advantages to implementing a network monitoring tool:
- Improved network uptime and reliability
- Increased security and threat detection capabilities
- Greater efficiency and productivity
- Reduced operating costs
So, what features should you look for in a network monitoring tool? Consider these key features:
- Real-time monitoring and alerts
- Customizable alerts and automation
- Scalability and flexibility
- Intuitive user interface and reporting
- Integration with other tools and systems
With the right network monitoring tool, you can quickly diagnose and resolve performance issues, improve uptime, and optimize your network's functionality. So don't wait until you start experiencing problems – invest in a network monitoring tool today and keep your network running smoothly!