LAN Subnet: What You Need to Know
When it comes to networking, choosing the right LAN subnet can make or break your network. A LAN subnet, also known as a local or private network, refers to a group of devices that are part of the same network and are able to communicate with each other without the need for a gateway or router.
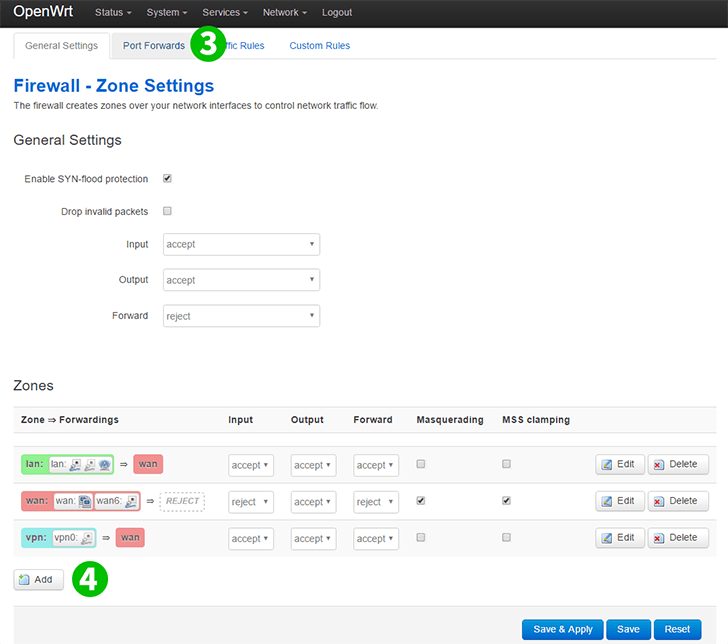
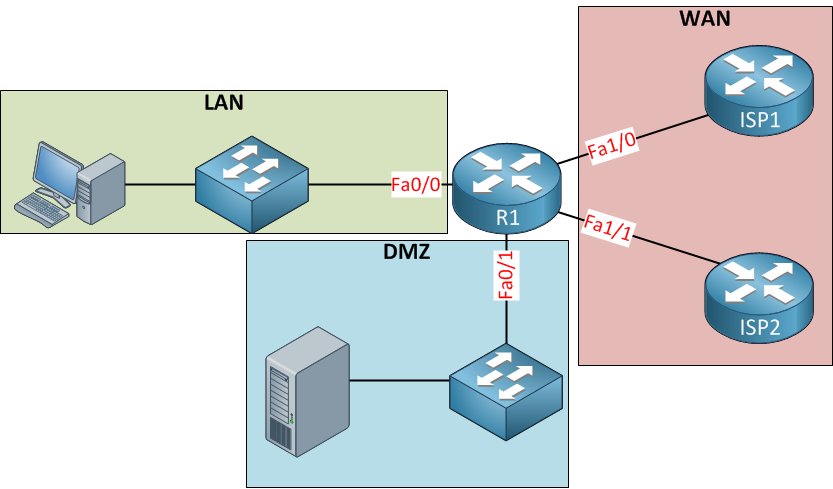
By dividing your local network into subnets, you can increase network performance and security, as well as efficiently manage network resources. Subnets are typically separated based on location or function, and each subnet is assigned a unique IP address and subnet mask.
One of the primary benefits of using a LAN subnet is that it allows you to control the flow of network traffic between different devices on the network. This helps to prevent unauthorized access and reduces the risk of network congestion or outages. Additionally, subnets can be used to isolate particular devices or groups of devices in the event of a security breach or other network issue.
When setting up a LAN subnet, it's important to ensure that all devices on the network are configured correctly and are using appropriate IP addresses and subnet masks. You may also need to configure routing tables and other network settings to ensure that traffic is routed efficiently between different subnets.
Ultimately, choosing the right LAN subnet for your network depends on your specific needs and requirements. Whether you're looking to improve network performance, increase security, or simply better manage your network resources, subnets can be an invaluable tool for achieving your goals.