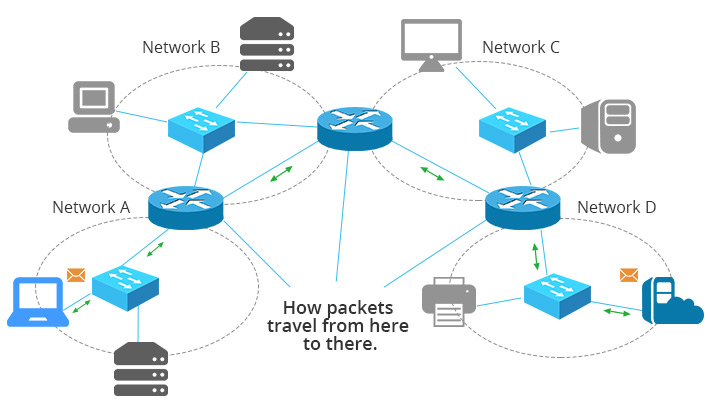
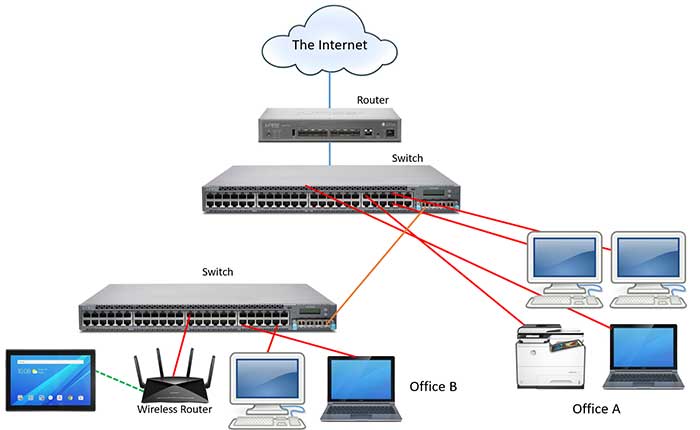
Are You Bored? Let's Test Your Router!
We all know how important it is to keep our routers working correctly. These little devices keep us connected to the internet and allow us to watch funny cat videos to our hearts' content. But have you ever stopped to wonder if all of your router's ports are working correctly?
No? Well, then it's time to liven things up and test those ports! It's like taking your router to the doctor for a check-up. So, grab a cup of coffee, put on some lively music, and let's get started with some easy steps.
Step 1: Look at your router's LED lights. They should be blinking to indicate that the router is functioning correctly. If not, you'll need to troubleshoot the issue until the lights are blinking again.
Step 2: Connect your computer to your router's LAN port, which is usually labeled "LAN" or "Ethernet."
Step 3: Open up your web browser and type in your router's IP address. Once you're logged in, navigate to the "Port Forwarding" section.
Step 4: Choose a port number, any port number, and enter it into the port forwarding settings. Remember to save your changes!
Step 5: Use an online port scanning tool to test that port. You should receive a message that says the chosen port is open. If the message says the port is closed, you'll need to troubleshoot the issue.
Following those steps will make it easy to test your router's ports. As you can see, the process is straightforward and quick. Plus, you'll be all caught up on your "router maintenance." So, what are you waiting for? Go ahead and test those ports!