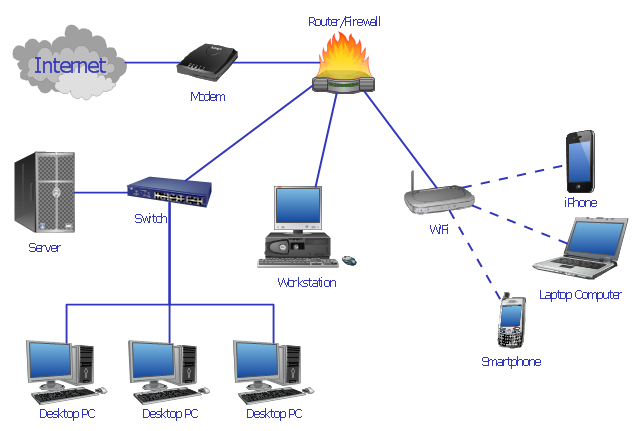
Network DMZ: The Gateway to Bulletproof Network Security
Do you know what DMZ stands for in the world of network security? DMZ is the abbreviation for the term Demilitarized Zone, which refers to a physical or logical network segmentation scheme used to isolate an organization's internal network from external networks. The DMZ is often regarded as the gateway to bulletproof network security, as it acts as the first line of defense against malicious attacks.
In simple terms, a Network DMZ acts as a neutral or buffer zone that's located between the internet and an organization's internal network. All traffic that passes through the DMZ is subject to more stringent security measures, including firewall rules, port forwarding, and packet filtering. The DMZ mechanism makes it difficult for attackers to penetrate your network and gain unauthorized access to your data.
By implementing a Network DMZ, organizations can alleviate many of the risks associated with exposing critical infrastructure to the internet. It's an effective risk management strategy that enables network administrators to exercise greater control over inbound and outbound traffic, restrict access to certain services, and reduce the impact of potential security breaches.
In conclusion, establishing a Network DMZ is a critical step in ensuring the safety and security of your organization's network infrastructure. It serves as the first line of defense against cyberattacks and offers a high level of protection against unauthorized access. Don't wait until it's too late; set up your Network DMZ today and enjoy the peace of mind that comes with knowing your assets are well-protected.