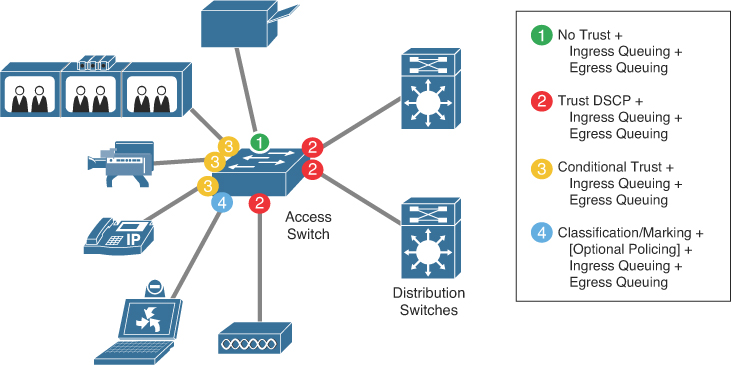
Router VPN client
Router VPN client
In today’s competitive and constantly evolving digital age, the security of sensitive online data has become paramount. As a result, virtual private networks (VPNs) have become increasingly popular, with people using them to secure their online activities and protect their privacy. This has led to the development of router VPN clients that offer a more convenient way for people to secure their network.
A router VPN client enables the VPN connection to be established through the router itself, meaning all devices that connect to the router are automatically secured by the VPN. This eliminates the need to set up VPN connections on individual devices, making it a more efficient and effective way of securing online activities.
One of the benefits of using a router VPN client is that it protects all internet-connected devices within the network without the need for any additional software or configuration. This means that devices such as Smart TVs, gaming consoles, and even IoT-enabled devices can be protected using the VPN. This allows for a seamless and secure browsing experience, without any interruption.
Moreover, a router VPN client can also help people bypass geographic restrictions on certain websites and services. This is particularly useful for people who travel frequently, as they can easily access region-restricted services and content from anywhere in the world.
As with any technology, choosing the right router VPN client is crucial. Factors such as speed, security, and compatibility should be considered before making a decision. Additionally, users should also ensure that their router is compatible with the VPN provider they choose.
In conclusion, a router VPN client offers an effective and convenient way to secure online activities and protect privacy. By ensuring all devices within the network are secured, it eliminates the need for setting up VPN connections on individual devices, providing an uninterrupted and seamless browsing experience.