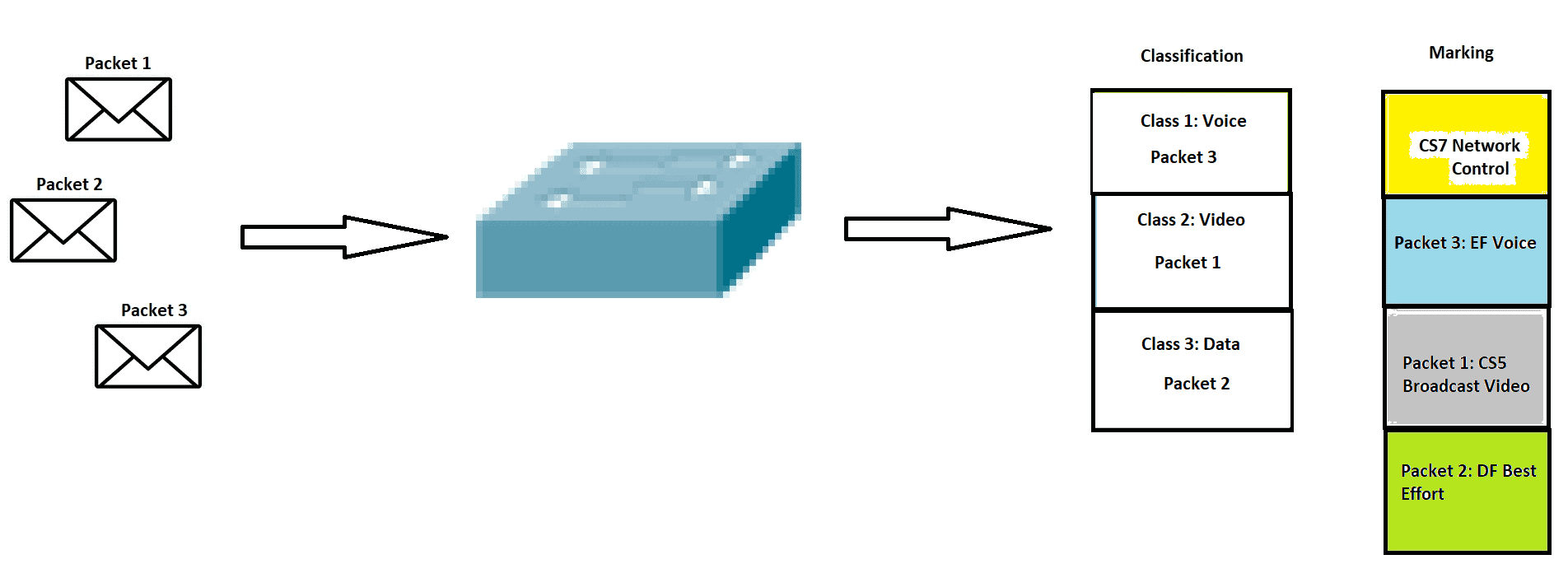
Network Traffic Sniffing: An Overview
Network traffic sniffing is the process of capturing network data packets passing through a specific network interface. It is usually done for monitoring and troubleshooting purposes, but it can also be used maliciously by hackers to obtain sensitive information.
By capturing data packets, network traffic sniffers can analyze and interpret the data to gain insights on various aspects of network traffic, including the source and destination of packets, the protocols being used, the type of data being transmitted, and more. This information can be used to identify network performance issues, troubleshoot connectivity problems, and detect and prevent network intrusions.
One of the most common types of network traffic sniffing tools is the network protocol analyzer or packet sniffer. These tools allow users to capture, decode, and analyze network traffic in real-time. Some of the popular packet sniffers in use today include Wireshark, tcpdump, and Snort.
While network traffic sniffing can be useful for legitimate purposes, it can also be used for malicious activities like cyber espionage, data theft, and network reconnaissance. To prevent unauthorized sniffing of network traffic, organizations should implement security measures like encrypted communications, intrusion detection and prevention systems, and network segmentation.
In conclusion, network traffic sniffing is an essential tool for network administrators and security professionals. However, it also poses a significant security risk if used maliciously. Organizations must take appropriate measures to protect their networks from unauthorized sniffing and other security threats.