Wireless Network Map – An Essential Tool for Businesses
Wireless networks have become an integral part of businesses. They have revolutionized the way we operate, communicate and exchange data. However, managing and optimizing wireless networks can be a complex task for IT administrators. This is where the wireless network map comes in as an essential tool.
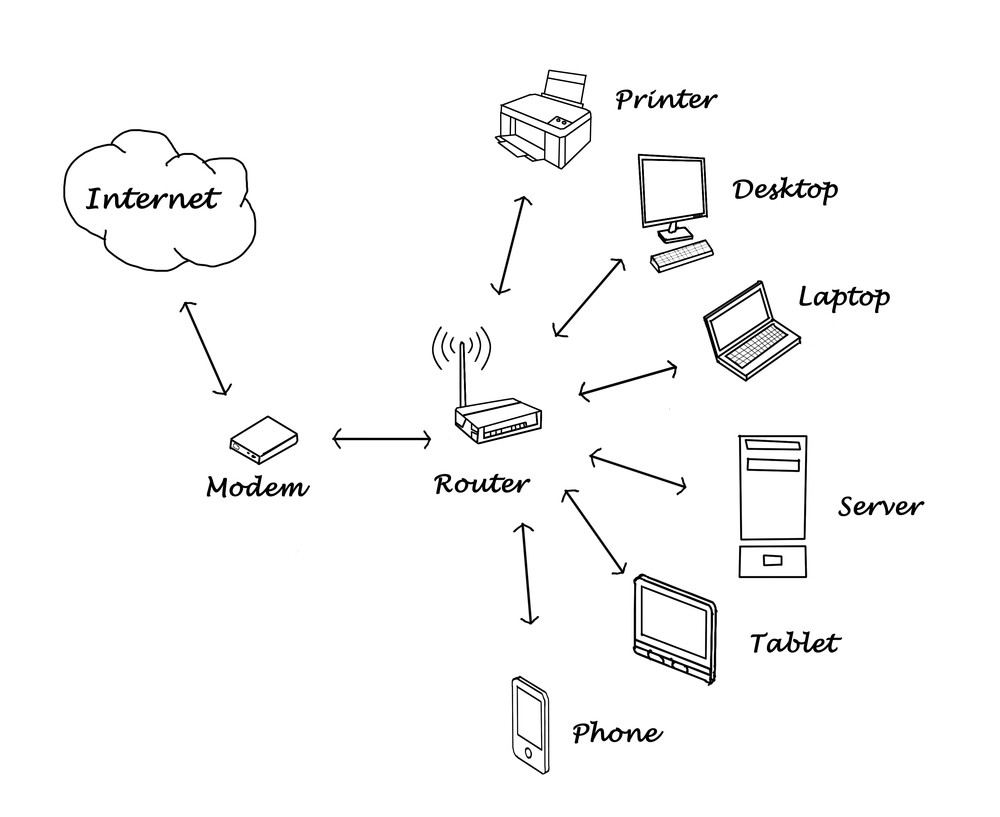
A wireless network map is a graphical representation of the wireless network infrastructure. It displays the network topology, access points, routers, switches, and other network devices. It also shows the connections between the devices, the signal strength, and the network traffic flow. The map enables IT administrators to visualize the network layout and monitor the performance in real-time.
The wireless network map provides several benefits to businesses. Firstly, it helps in troubleshooting network issues. IT administrators can quickly identify the devices causing network disruptions or congestion and take corrective measures. Secondly, it helps in optimizing the network performance. By analyzing the network traffic data, IT administrators can make informed decisions about network upgrades, capacity planning, and security measures. Thirdly, it empowers businesses to improve network security. The map shows the location of all devices, making it easier to identify unauthorized devices.
In conclusion, the wireless network map is an essential tool for businesses to manage, monitor, and optimize their wireless networks. It provides a clear visual representation of the network infrastructure, enabling IT administrators to troubleshoot issues, optimize performance, and improve security. As wireless networks become more complex, the wireless network map becomes a crucial component of business operations.